


Companies specializing in finance, healthcare, and insurance deal with sensitive data sets of customers such as PCI (Payment card industry), PHI (Protected health information), and PII (Personally identifying information). They need to comply with regulations such as PCI-DSS, HIPAA, and so on. Sensitive data is transferred between various systems such as payment, customer care, collection, risk, and analytics. Because of compliance, companies must encrypt the sensitive data in these systems and implement rigid authentication, audit, and access controls. When regulators conduct audit, they must verify the systems, thereby making the process very costly. Every system is not required to include sensitive data in encrypted form. Companies can utilize tokenization and store tokens instead of encrypted original sensitive data. Tokens do not have value even when they are stolen. Implementing tokenization makes systems more secure and reduce cost. This page describes the basics of tokenization and how InsightLake's tokenization solution help companies secure, simple, and make their sensitive data storage cost effective.
In encryption, a secret key is used to encrypt the original data. Keys are stored at a secure place. If a hacker gets hold of keys or uses brute force to generate one, he can decrypt the data. Systems that hold PHI, PII, and PCI data in encrypted form are subjected to string compliance and audit. In tokenization, data is replaced with another un-related token value; no mathematical algorithm is used. If a hacker gets the token value, he cannot generate the original data. Systems that hold tokenized data are not subject to strict compliance requirements, which reduces cost and risk. Tokenization makes implementation easier and less expensive. Both encryption and tokenization work together to build a layered security architecture, which is compliant with regulations. InsightLake's tiered security architecture allows companies to comply with regulations such as PCI and HIPAA, in a cost effective way while achieving maximum security. It is essential to reduce the flow of sensitive data between systems and secure both in transit and at rest. Tokenization makes sensitive data secure and cost effective. Tokenized data has no value, and systems that store tokenized data can manage compliance without rigid security and audit requirements. Token mappings are stored in secured encrypted data store, which comply with regulations. All access to mapping stores are tracked and audited. InsightLake’s Tokenization Solution uses strong encryption and key management with effective and flexible tokenization. It allows companies to leverage scalable token generation and secure storage. It also allows them to use variety of token formats or design a custom format to tokenize all data types. Generated tokens and mappings are stored in secure encrypted storage systems, which are PCI-DSS and HIPAA compliant.
InsightLake’s Tokenization Service enables REST endpoints to invoke service for tokenization and de-tokenization.
Endpoint must pass the following parameters to tokenize the data. Endpoint key - secure first time registration key to use the API Token format - variety of formats to choose from Category PII, PHI, PCI - for compliance and
audit logging Data Value Tokens are generated using secure mechanisms such as completely random generation, one way non-reversible hash, and custom proprietary way.
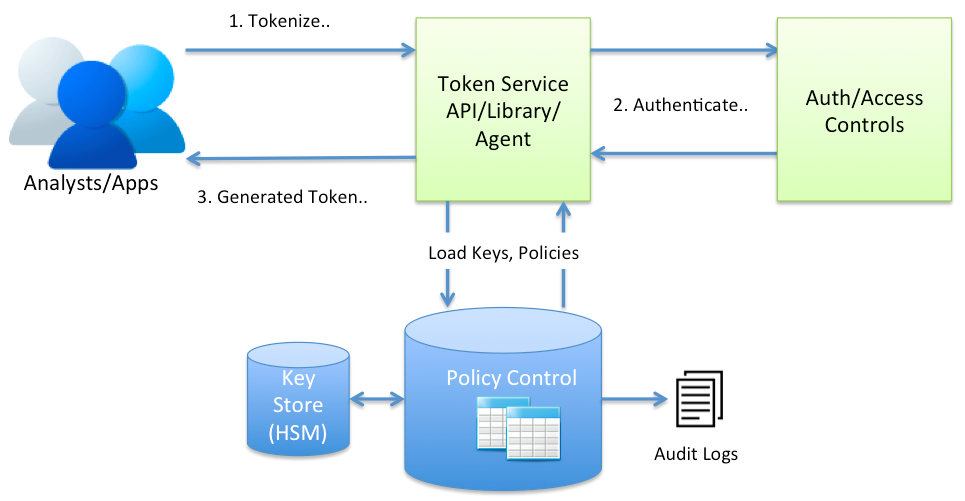

Vault-less scalable tokenization service generates token based on the format (alpha numeric) supplied while preserving the data format. All interactions to tokenize and de-tokenize are captured in audit logs and monitored. Users cannot download more than 1000 clear entries in a given period to comply with the regulations. Tokenization system complies with regulations such as PCI-DSS, and HIPAA, and generates regular audit reports. Format preservation allows companies to not change data models, gain intelligence in the data without losing any value.
Well designed REST API and Java library allows developers to tokenize and detokenize the data easily. Tokenization framework connects with central policy controller for policies, keys and user roles. Framework applies role based seperation
of duties internally hidden from developers.
Security agents or enforcement library are the main actors, they load policies from central policy server, apply policies (encryption, tokenization/de-tokenization based on roles), generate alerts, modify queries for data protection
and capture audit logs.
Systems that store transactions, and customer data for analytics do not require PII, or PCI data sets other than joining information. Encryption poses a challenge because secure keys must be distributed for analytics, which increases risk for sensitive data leakage and it degrades performance. Tokenization makes the solution secure without any performance impact.
