Data Security - Monitoring & Protection
Enterprises today are storing large amount of data in data lakes and data stores to gain insights. At the same time regulations like Sarbanes-Oxley, HIPAA, GDPR are forcing companies to protect sensitive data sets and conduct regular audits. Non compliance
can lead to legal action, reputation damage and business loss.
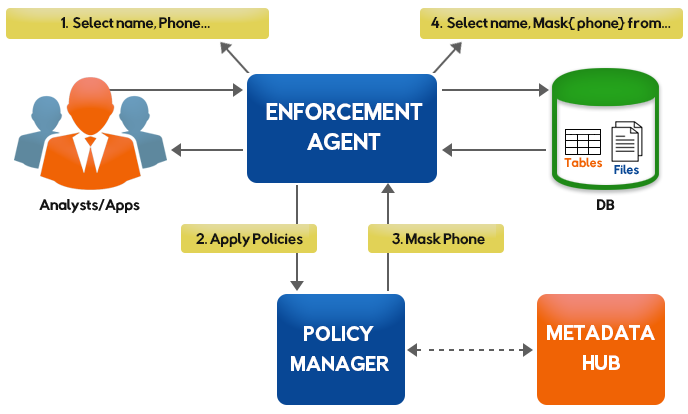
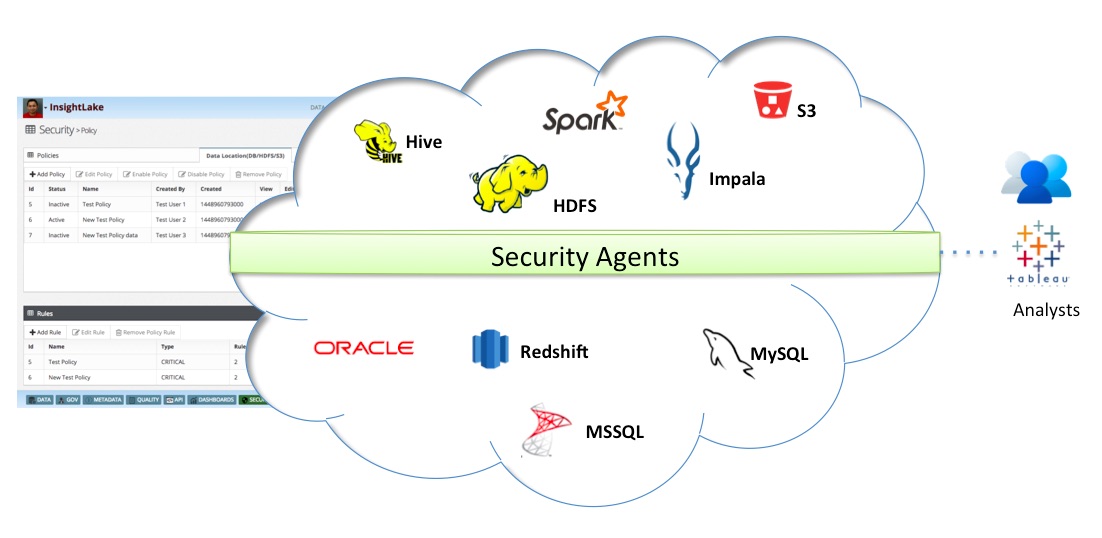
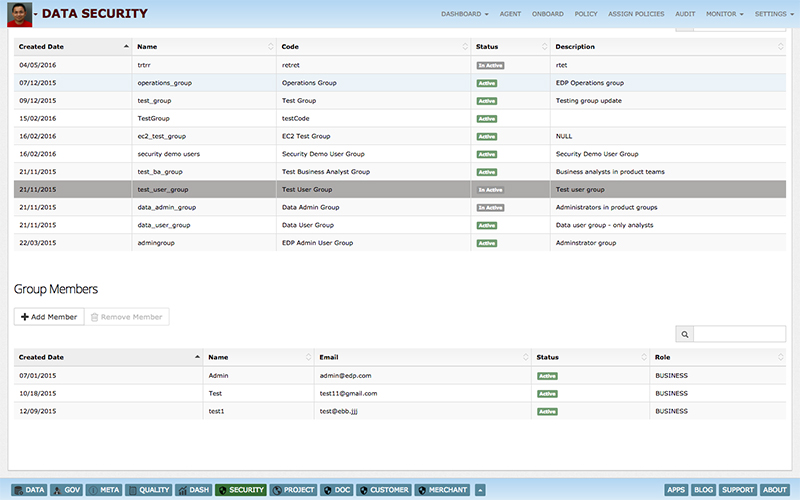
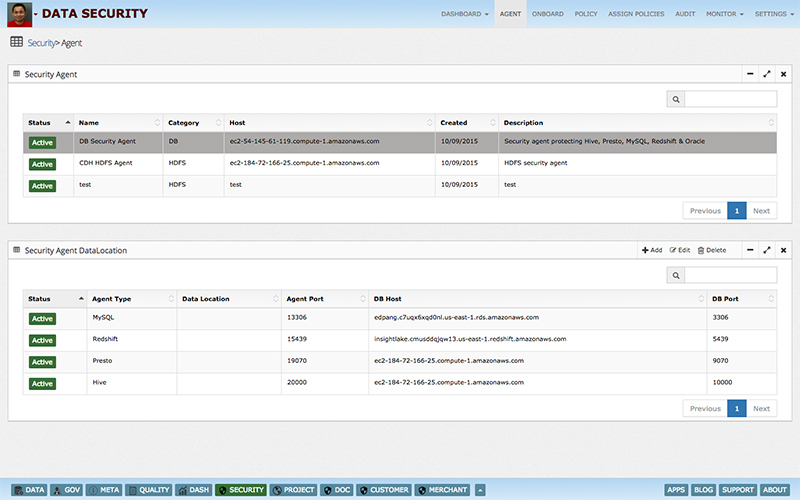
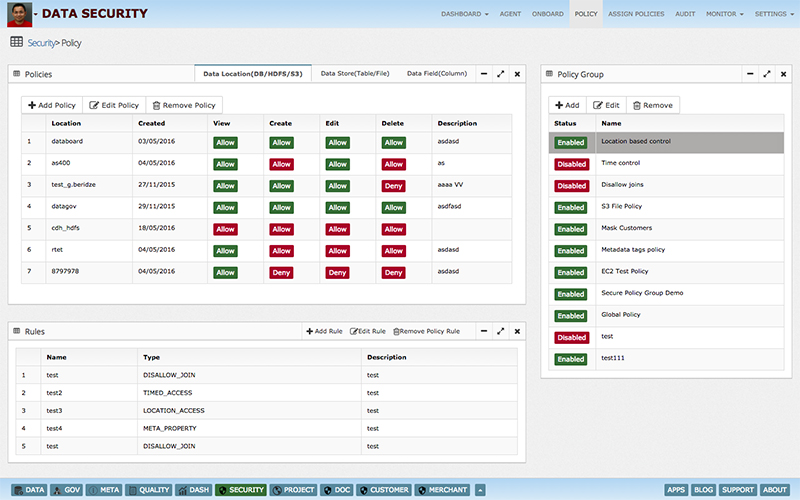
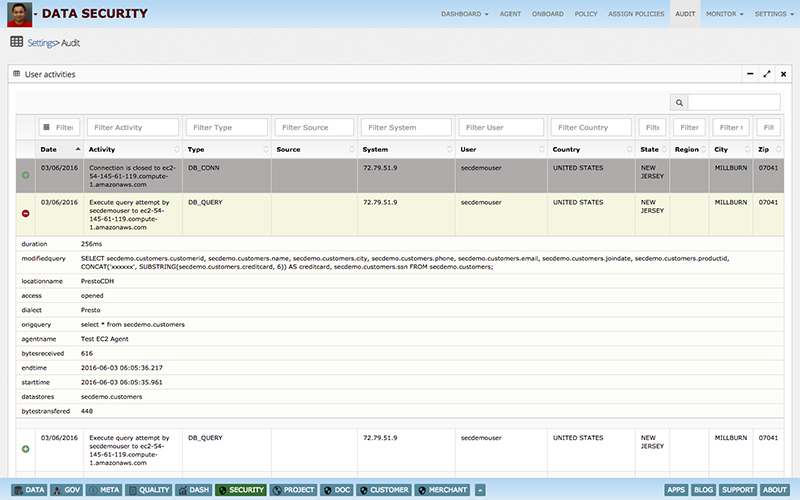
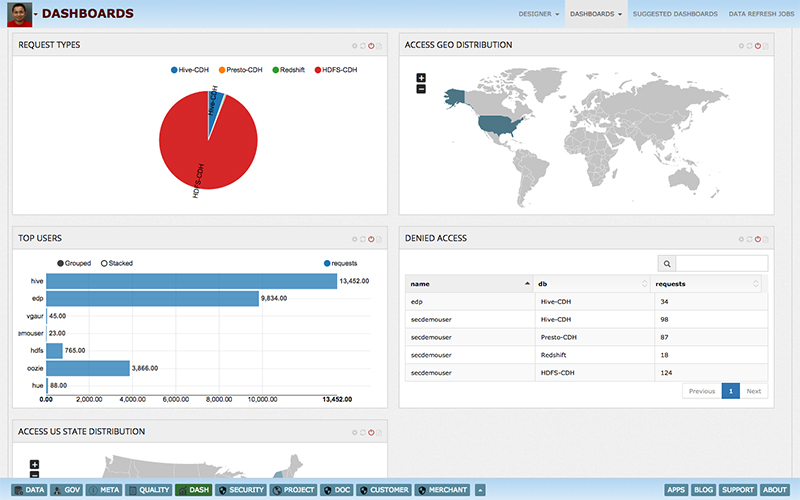
This poses a big challenge for enterprises to manage data access security in a central and easy manner. Data centric audit & protection (DCAP) solutions enable enterprises to discover, monitor, protect & audit data
effectively.